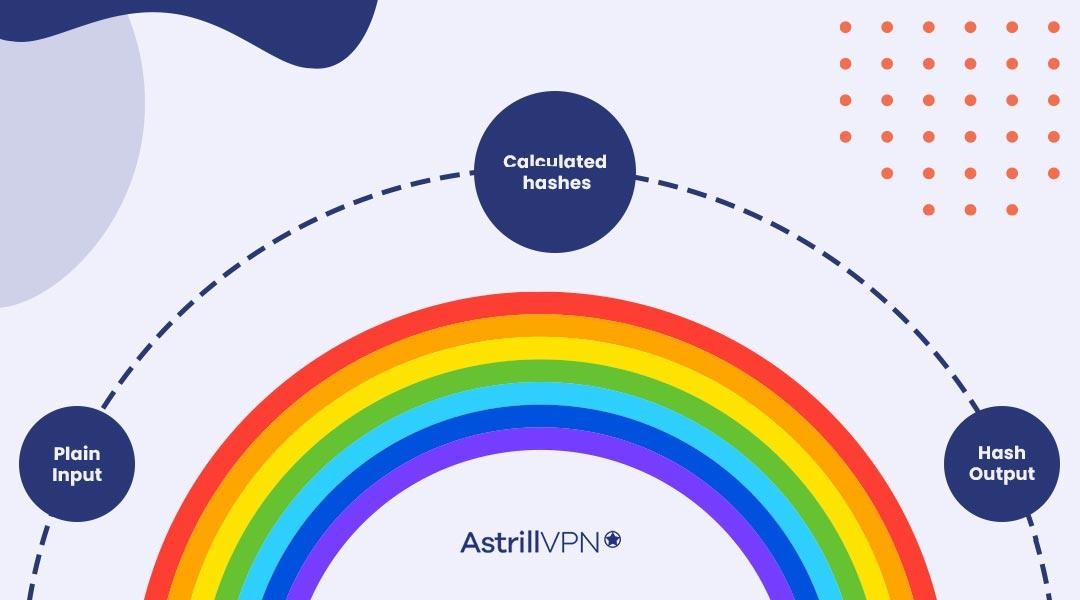
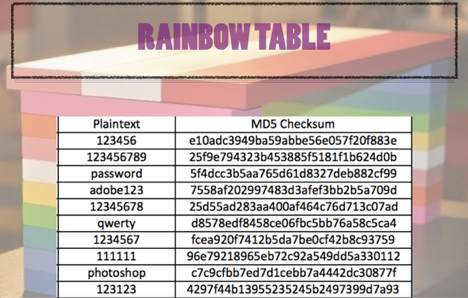
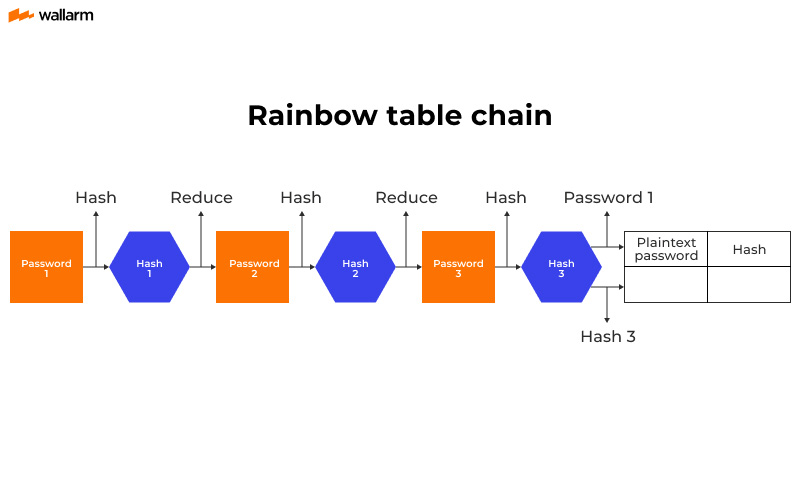
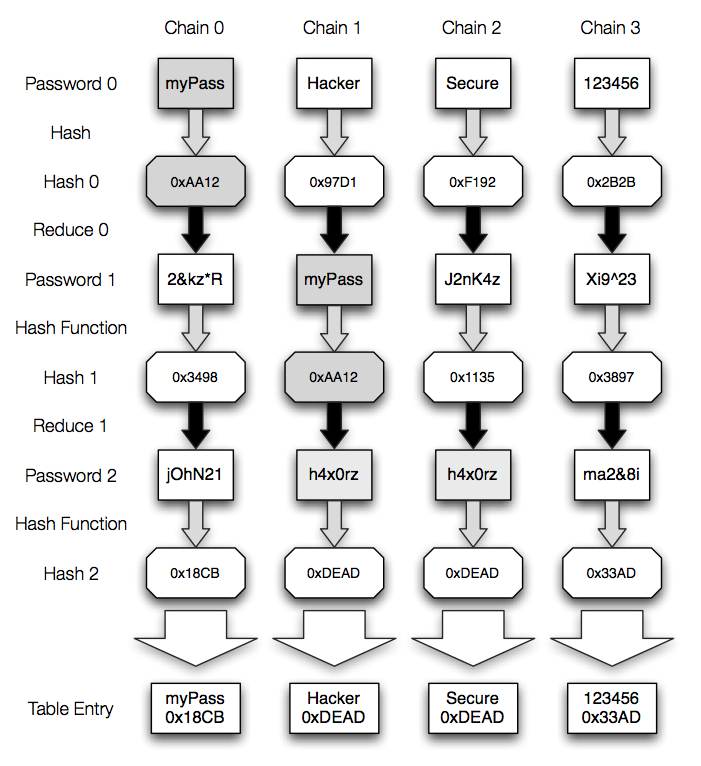
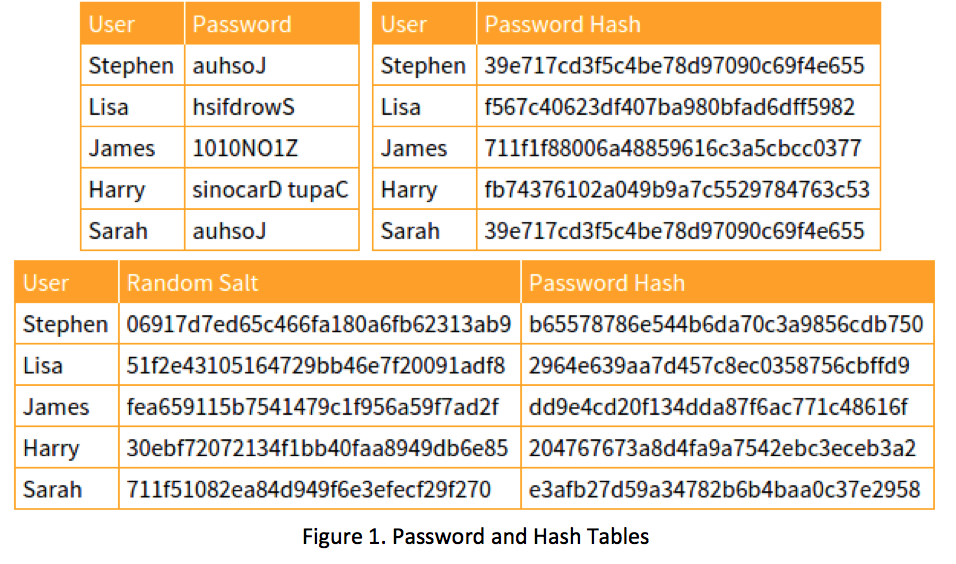
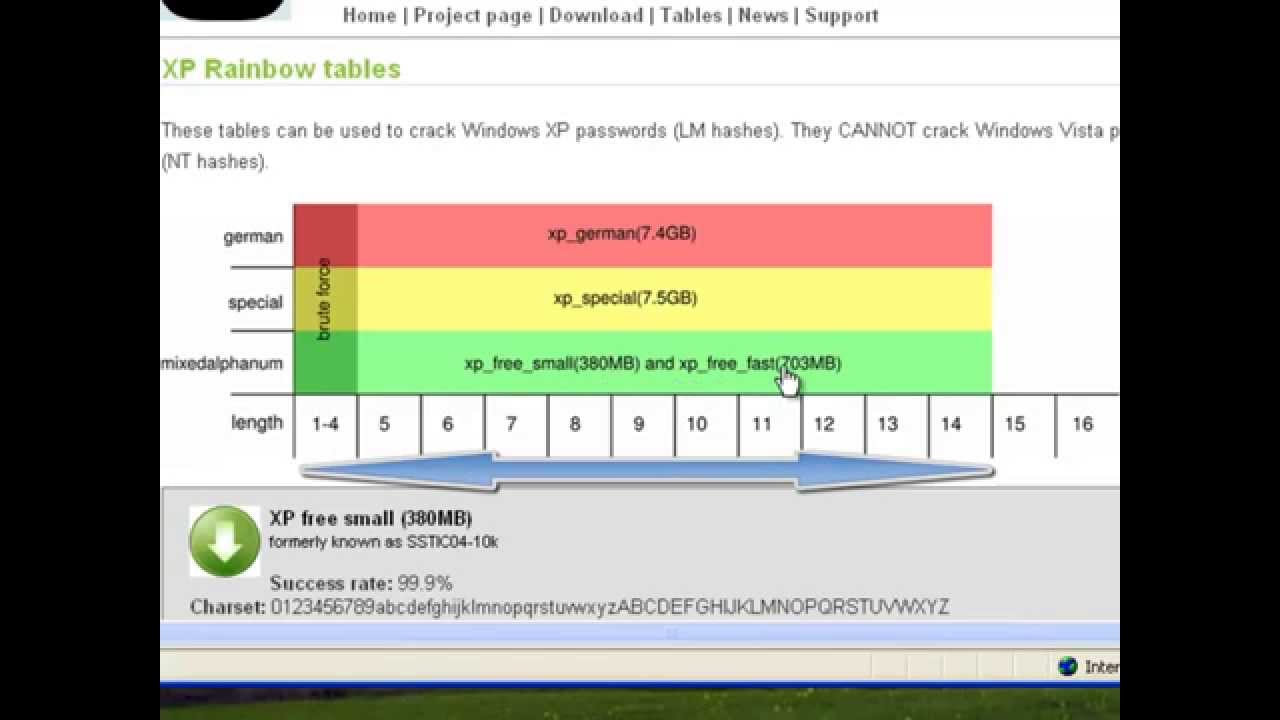
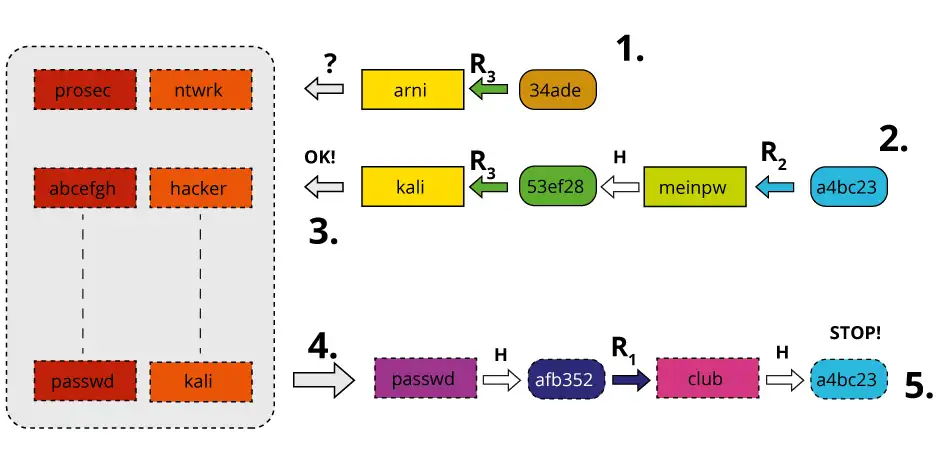
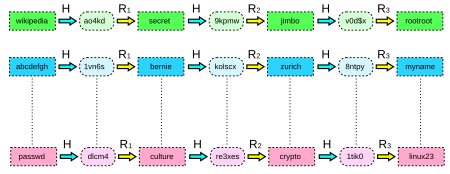
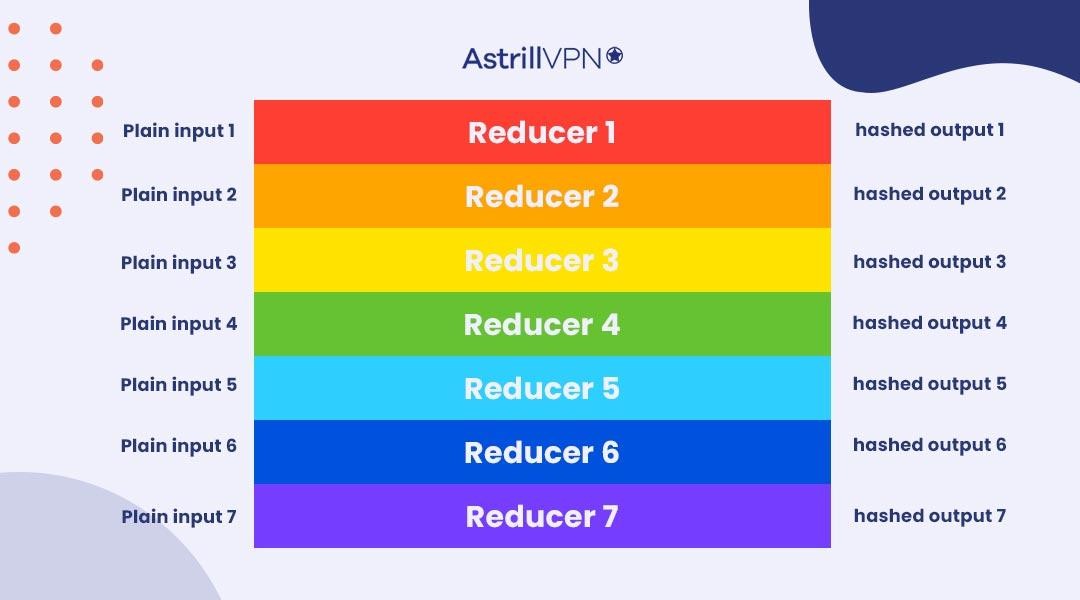
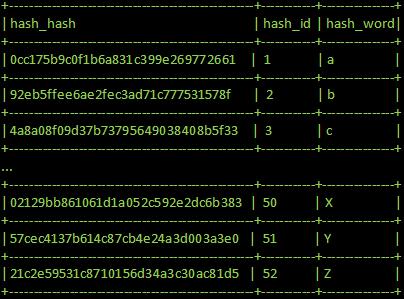
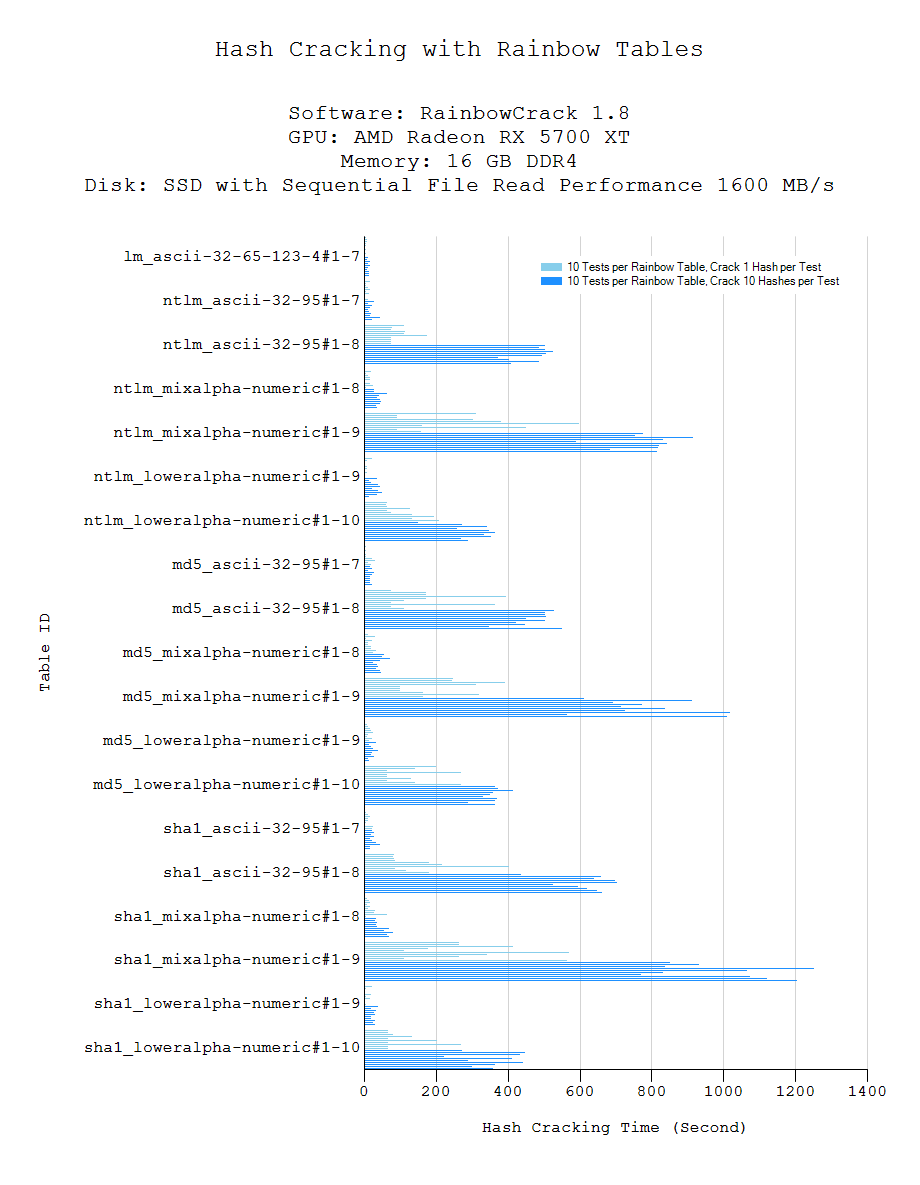
Prof B Buchanan OBE on X: "Be worried about the power of the Cloud to crack hashed passwords ... the threat is not rainbow tables anymore, but Hashcat rules. You say that
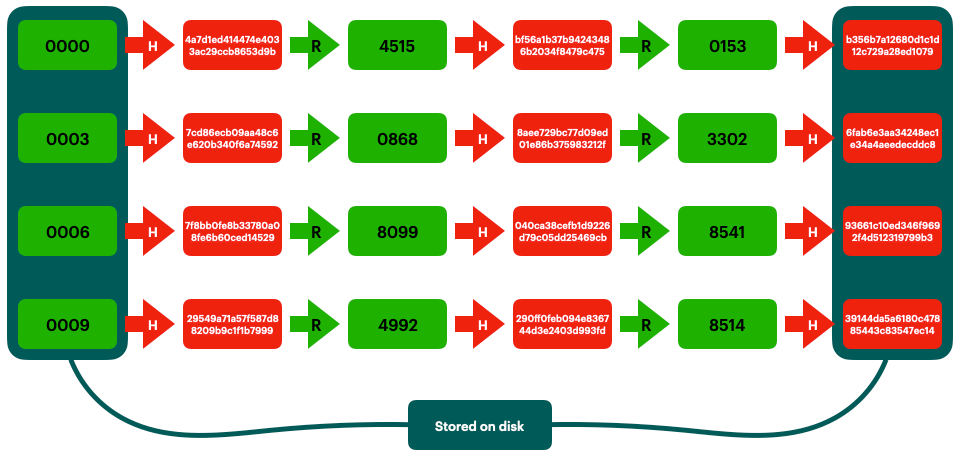
Rainbow Tables (probably) aren't what you think — Part 1: Precomputed Hash Chains | by Ryan Sheasby | Medium