IDA view: resolving ReadProcessMemory and checking relocation table size for asycfilt.dll – Security Over Simplicity
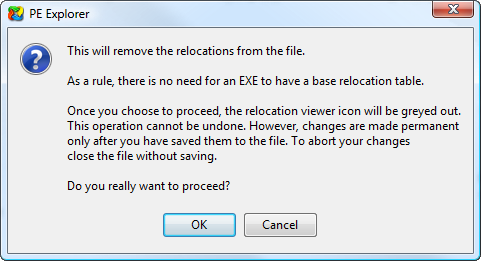
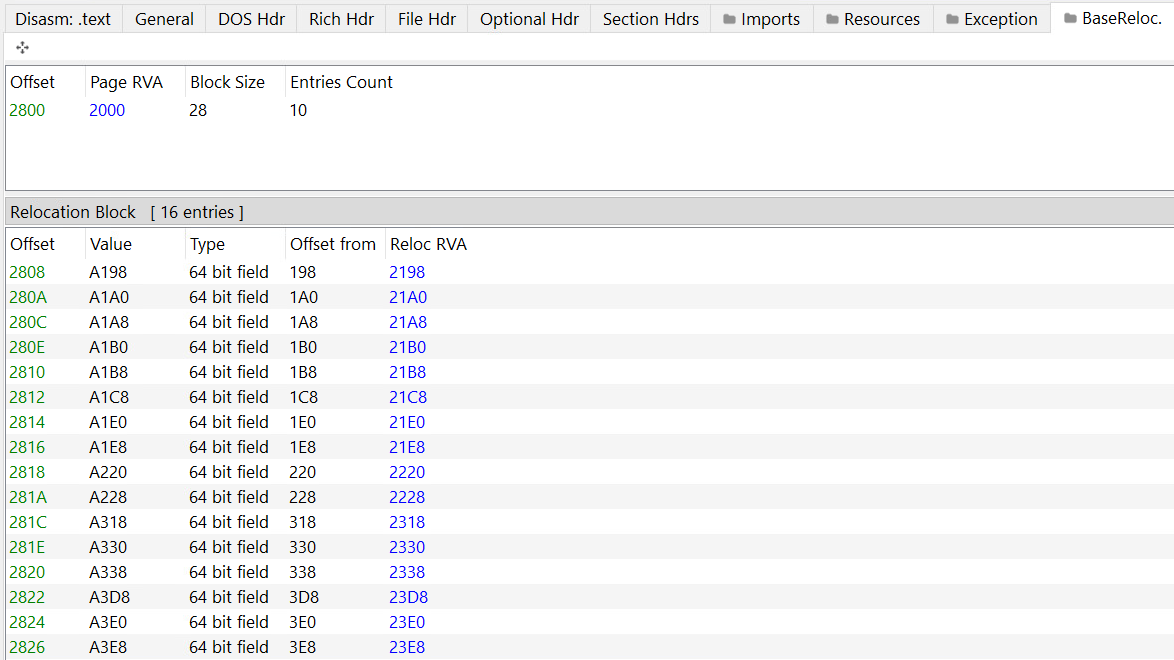
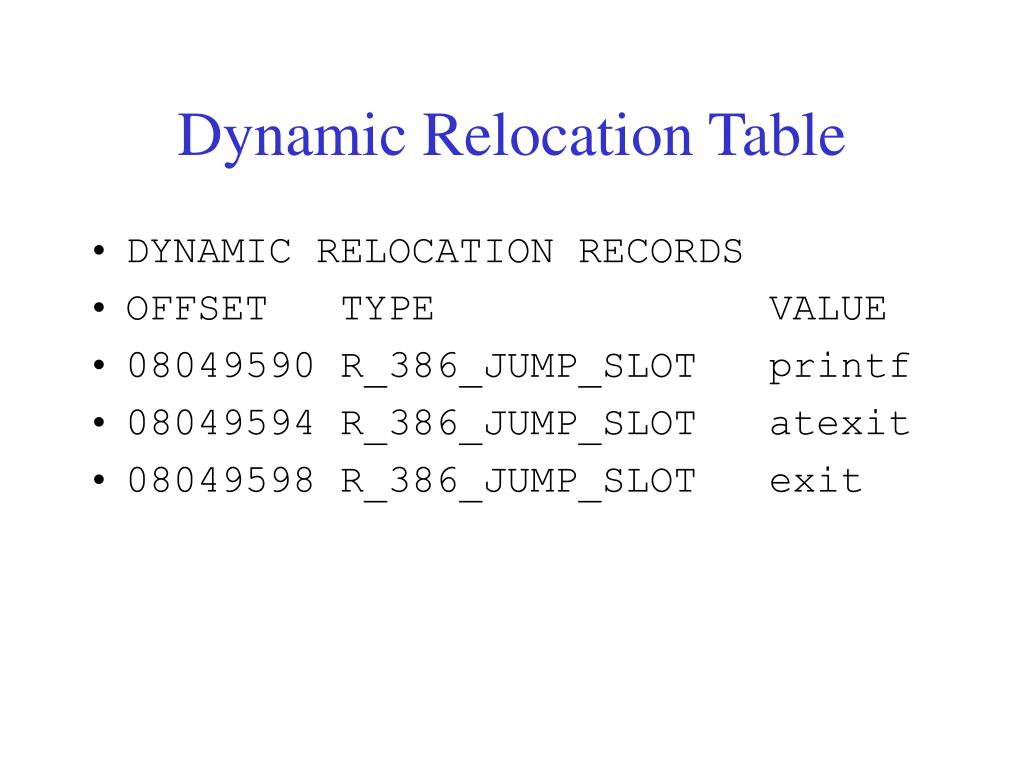
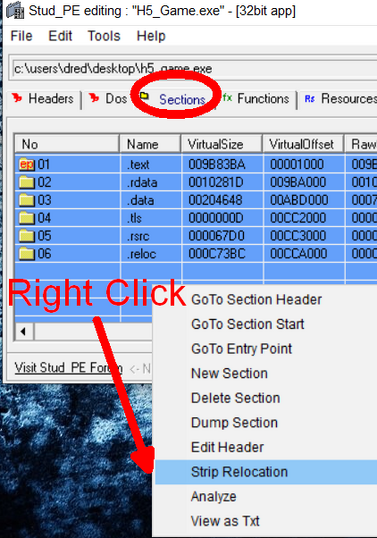
PE Explorer: Relocation Viewer. Relocations Removal Tool removes Base Relocations from EXE, Fix-Up Table.
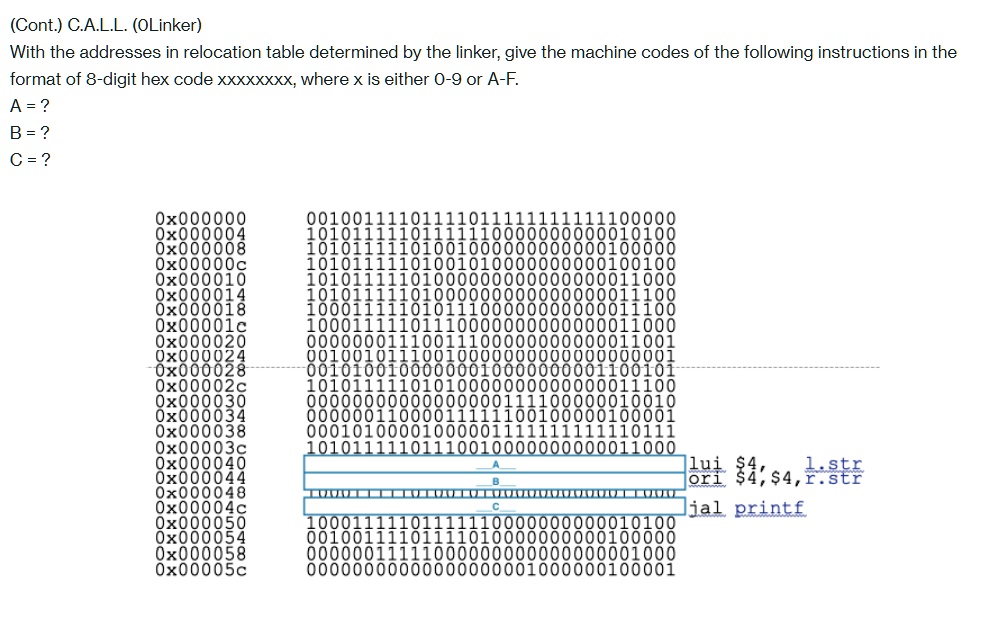
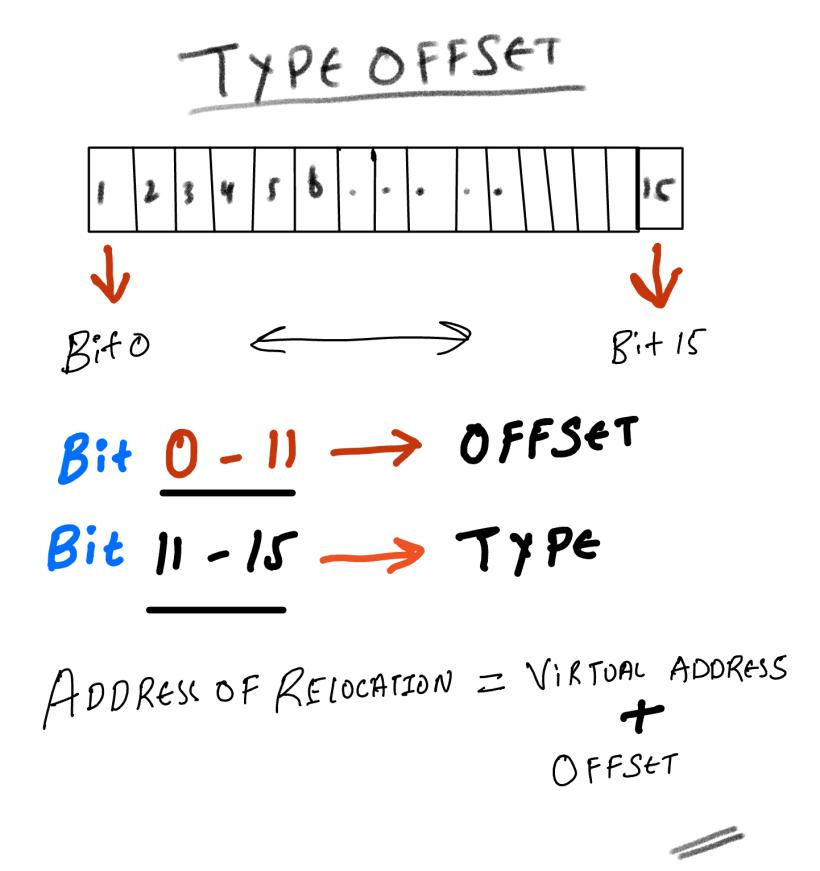
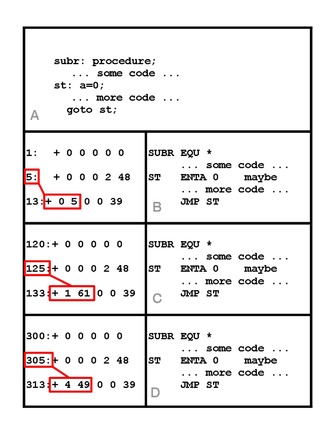
SOLVED: Text: (Cont.) C.A.L.L. (Linker) With the addresses in the relocation table determined by the linker, give the machine codes of the following instructions in the format of 8-digit hex code xxxxxxxx,

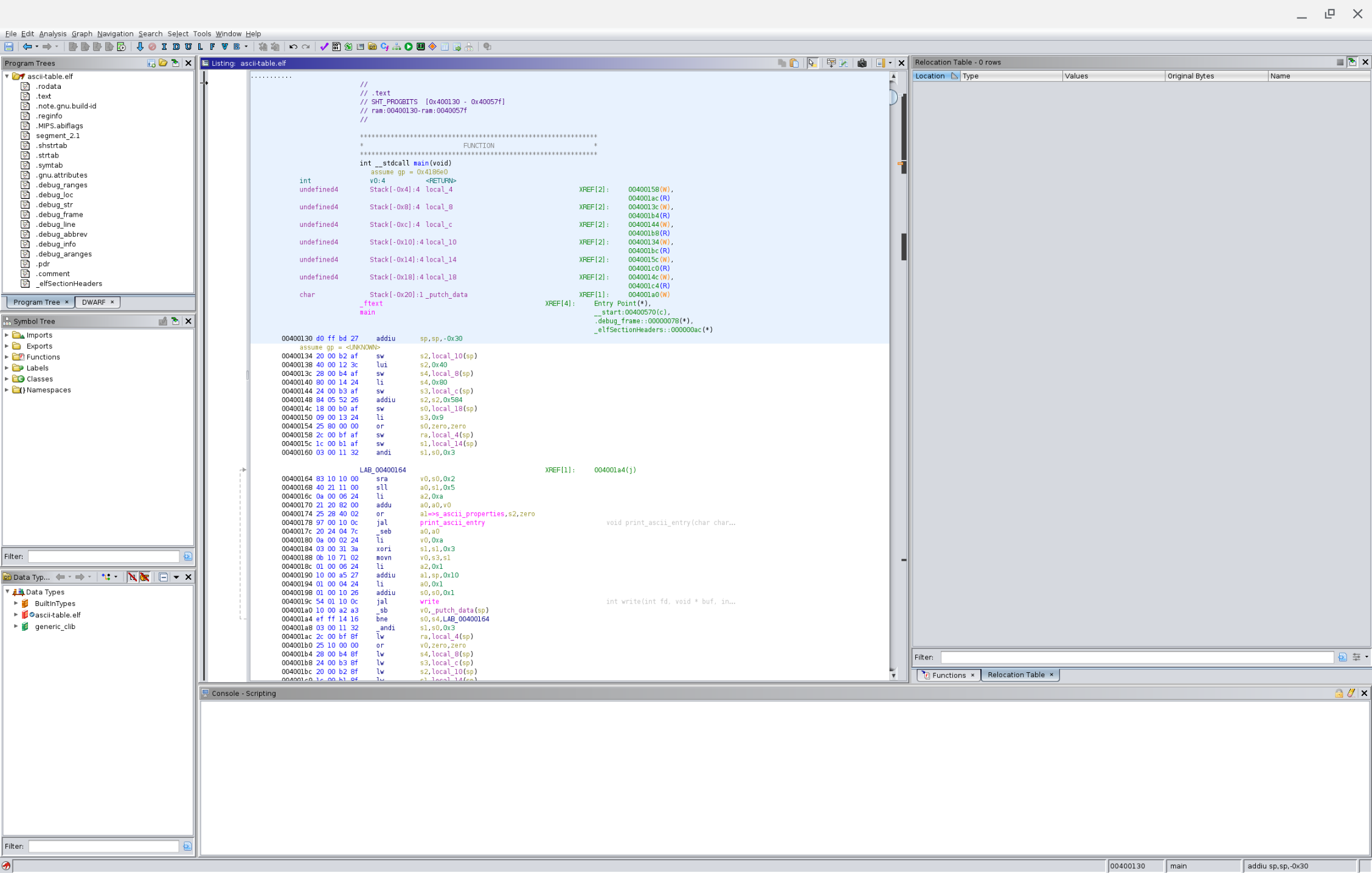
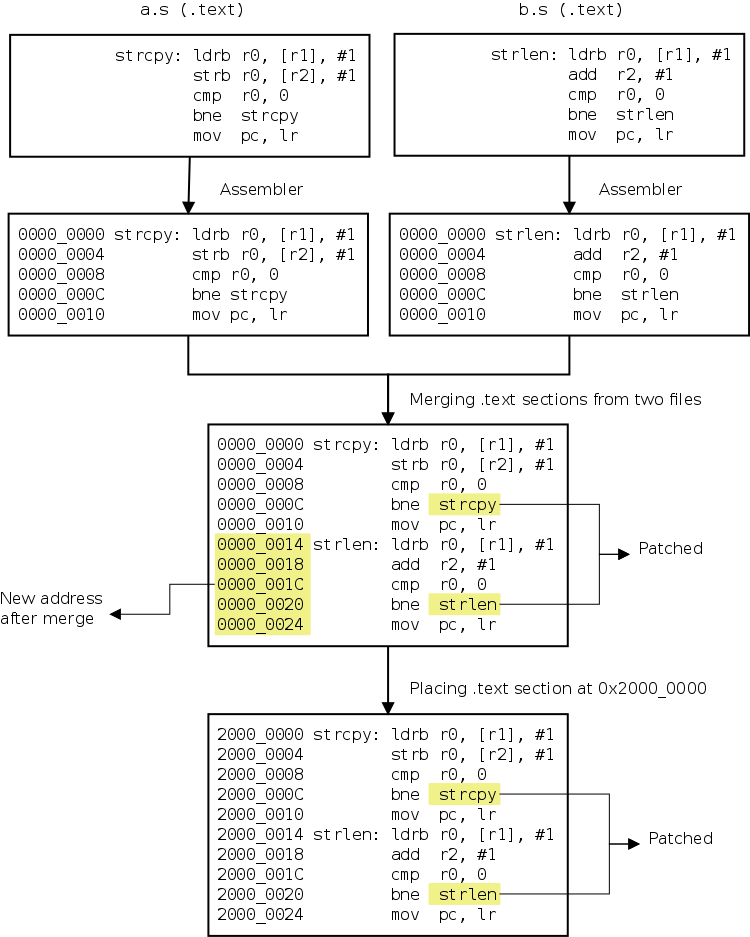
patching - IDA/Olly changing address bytes after patch during debugging on x86 - Reverse Engineering Stack Exchange